Types of access control systems
Access control systems help simplify managing access to a building but solutions have vastly different experiences.
Nexkey smartphone access control system
A key purpose of commercial access control systems is controlling access. Traditional systems have been centered around this aim yet access control has evolved more in the last year than the last decade.
Modern platforms have emerged with added features that provide a lot of business value beyond access management. Now we see an emergence of intelligent reporting and insights from Dashboards, user and admin messaging, automated workflows through integrations, and remote access.
These features have been essential for businesses post-pandemic, in this new normal, to reopen and run their business as safely and efficiently as possible.
This article will help you to understand what is provided, features, experience, and maintenance for each access control system.
Cloud versus on-premise
Historically, access control systems were first on-premise systems but software-as-a-service has been gaining popularity. The adoption of the cloud has allowed smaller businesses with less resources and time to have access control.
While most businesses now use a cloud system, there are still use cases where an on-prem or perhaps a hybrid solution can make more sense.
On-premise access control system
Some organizations prefer the legacy access control systems, namely on-prem systems, where they have more control. Peripheral devices like readers, controllers, and access control panels are all connected to a central computer that serves as the main server.
Instead of paying a monthly fee, companies typically need to pay a license fee for the software, and management of the system falls on their shoulders. On-premise access control systems are often found in bigger companies who can afford to have on-site IT teams who have the knowledge and experience to manage, monitor, and update these systems.
Cloud-based access control systems
Instead of having an in-house server to store the access list and audit trails, everything is stored in the cloud. Most businesses today use a cloud-based access control system, because it is easier to use and manage, more cost-efficient and has more opportunities to integrate with other software tools.
Still, not all are created equal. Cloud-based or SaaS enabled access control can look very different in terms of how the hardware is installed, whether the software is managed by admins, what credentials are used to access buildings, etc.
For the purpose of this guide, we will be focusing and diving into the different types of access control systems that utilize the cloud.
Basic components for your access control system
There are 3 main parts we will cover that make up access control systems, access management tools used by admins, hardware installed, and the user experience, specifically what users use to access the building. All will help determine what access control system is right for your business.
Access management tools
For most systems, access management would most likely mean a web portal or dashboard. More modern systems also have a mobile app to instantly grant access and monitor traffic.
Since the pandemic, more platforms have expanded their dashboards to include features like spatial utilization and occupancy reporting, advanced key management, and messaging features built into the software.
Hardware
Every system has different hardware components required. This section could have an entire blog post of its own. Here is some information on access control installation and how you can save money.
With some access control systems, you can retrofit using your existing door hardware. Depending on the platform, you may need to electrify your door with an electrified door strike or lever, or other door locking equipment like a maglock. An installation partner should visit your site and walk you through what you specifically need before giving you a quote.
Then there is the hardware of the access control system itself. In traditional access control, a reader is wired to electrified door hardware, and also to a door controller which adds connectivity and controls usually 1-2 doors. Those controllers are then connected to a main access control panel, which is the main connection to an on-prem or cloud network which stores access information to give the right people access at the right time.
It’s possible to cut out a lot of this hardware like readers and large access panels with some keyless, cloud-based access control systems, like Nexkey.
User experience
Most people buy access control for a simplified experience to manage access without giving out physical keys. But experience and security for the user is very important.
This starts with the access credential: a pin, key card or smartphone. The access control system will identify the credential and authenticate the user and then grants or denies access accordingly.
Access credentials
Credentials are the way users are authenticated by the access control system to have access, essentially the key to access physical spaces.
There are many ways that users can gain access, either by what they know, who they are, or what they have. Some methods are more secure than others, have a variety of different features, costs, and vastly different experiences.
What they know: Pincode or Password
Who they are: Biometrics (Fingerprint, Iris Scanner, Facial Recognition) or Phone Number
What they have: Fob, Keycard, or Mobile key
In traditional access control systems typically use key cards and fobs. Mobile is used in a low percentage of systems but it is quickly becoming more desirable among small- to medium-sized businesses who find key cards and fobs more of a headache to manage. Biometrics are still pretty rare, but are typically used in businesses with higher security requirements and larger budgets.
Which of the following access control credentials does your organization use for entry to the building?
| Benefits | Pincode | Fobs | Key card | Biometrics | Mobile |
|---|---|---|---|---|---|
| No need to rekey | X | X | X | X | X |
| No cost to make key | X | X | X | ||
| Complete audit trail | X | X | X | X | |
| Hard to copy | X | X | |||
| Can’t easily borrow | X | X | |||
| Always with you | X | X | |||
| Identity protected | X | X | |||
| Inexpensive system | X | X | |||
| Manage automatically | X | ||||
| Things to consider | |||||
| No backups if forgot | X | X | X | ||
| Hard to change for one user | X | ||||
| Shared without permission | X | X | X | ||
| Easily copied or stolen | X | X | X | ||
| Can’t track by user | X | ||||
| Manage manually | X | X | X | X | |
| Difficult and long installation | X | X | X | ||
| Expensive system | X | X | X |
Why is there a shift to mobile for access control systems in 2021?
Last July, Nexkey surveyed 1200+ office workers on how they feel about access control post-pandemic. 44% of respondents said they think access control is more important after COVID-19.
Nexkey mobile access control system
More and more businesses now need to manage a hybrid, flexible workforce. Nearly two-thirds of U.S. workers according to the Gallup poll will work remotely in some capacity even after the pandemic.
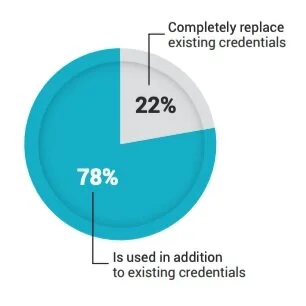
Mobile access control can ease a lot of the key management nightmares that still exist with keys, key cards, and fobs. The future is to be truly keyless, and business owners should be able to manage and monitor what is happening inside their businesses from anywhere.
No surprise, mobile credentials were the #1 choice in Nexkey’s 2020 Access Control Trends Survey when respondents were asked what they would like to use to unlock their doors, though only 5% currently use a smartphone to unlock their office.
According to HID’s 2019 survey, a leader in access control, 54% have upgraded or will upgrade to mobile access control in the next three years.